The term “data security” has become paramount in this digital age.
With the increased adoption of cloud computing, companies are no longer shackled by physical constraints and can expand their operations seamlessly.
However, this comes with a caveat: the obligation to ensure that sensitive data stored in the cloud is secure and well-protected.
This has led to the emergence of many cloud data security solutions designed to keep business information safe while being cost-effective and efficient.
We have collated 12 top-notch software that offers superior cloud data security solutions, catering specifically to the needs of small businesses.
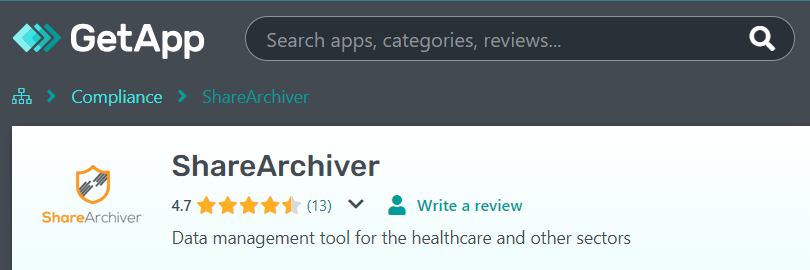
1. ShareArchiver
Founded to provide efficient and secure data storage solutions, ShareArchiver is a trailblazer in cloud providers of data security.
This software is designed with a high focus on security and efficiency without compromising on security compliance requirements, making it an exceptional choice for small businesses.
List of Features
- Secure Data Archiving
- Secure Access for Users
- Data Encryption Repository
- GDPR Compliance
- File Analysis and Reporting
- File Tagging and Indexing
- File Restoration
- De-duplication and Compression
- Storage Management
- Role-Based Access Control
Top 3 Features
1. Secure Data Archiving
ShareArchiver’s secure data archiving capability is powered by advanced encryption channels.
This feature ensures the integrity and confidentiality of your data during the archiving process.
It uses encryption algorithms to convert data into an unreadable form while storing, which can only be decrypted with unique decryption keys.
The loss or compromise of unencrypted data can have severe repercussions, including non-compliance penalties and reputation damage.
2. Secure Access for Users
ShareArchiver prioritizes user accessibility without compromising its approach to security.
It employs secure SSL connections and LDAP channels for user access.
This means that data in transit is protected by robust encryption, preventing unauthorized interception.
Secure access is crucial as cyber threats become increasingly sophisticated, with hackers often targeting data during transmission.
3. Data Encryption Repository
ShareArchiver uses this feature to ensure that all data at rest remains secure against any type of security threats.
The repository is like a vault where all the encrypted data is securely stored.
This means that even if someone were to gain unauthorized access to the repository, they wouldn’t be able to decipher the data without the decryption keys.
This feature is paramount, given the rise in data breaches involving unauthorized access to stored data.
Pros
- Exceptional data security with encryption-based archiving and access.
- Robust data storage management capabilities.
- Compliant with data protection regulations.
- Easy to execute and use.
- Requires no specialized training to familiarize with, or use the software.
- Effortless compatibility
Cons
- Difficulty in exporting logs
- Some feature names are confusing
Pricing
ShareArchiver offers tailored plans according to exclusive needs of each client. Interested clients can contact Sales department for a personalized price plan.
Customer Support
- Chat
- Help Desk
- Phone support
- 24/7 live rep
Available Platform Support
- Windows
- MacOS
Average Ratings
ShareArchiver ranks at 4.7 on both Capterra and GetApp.
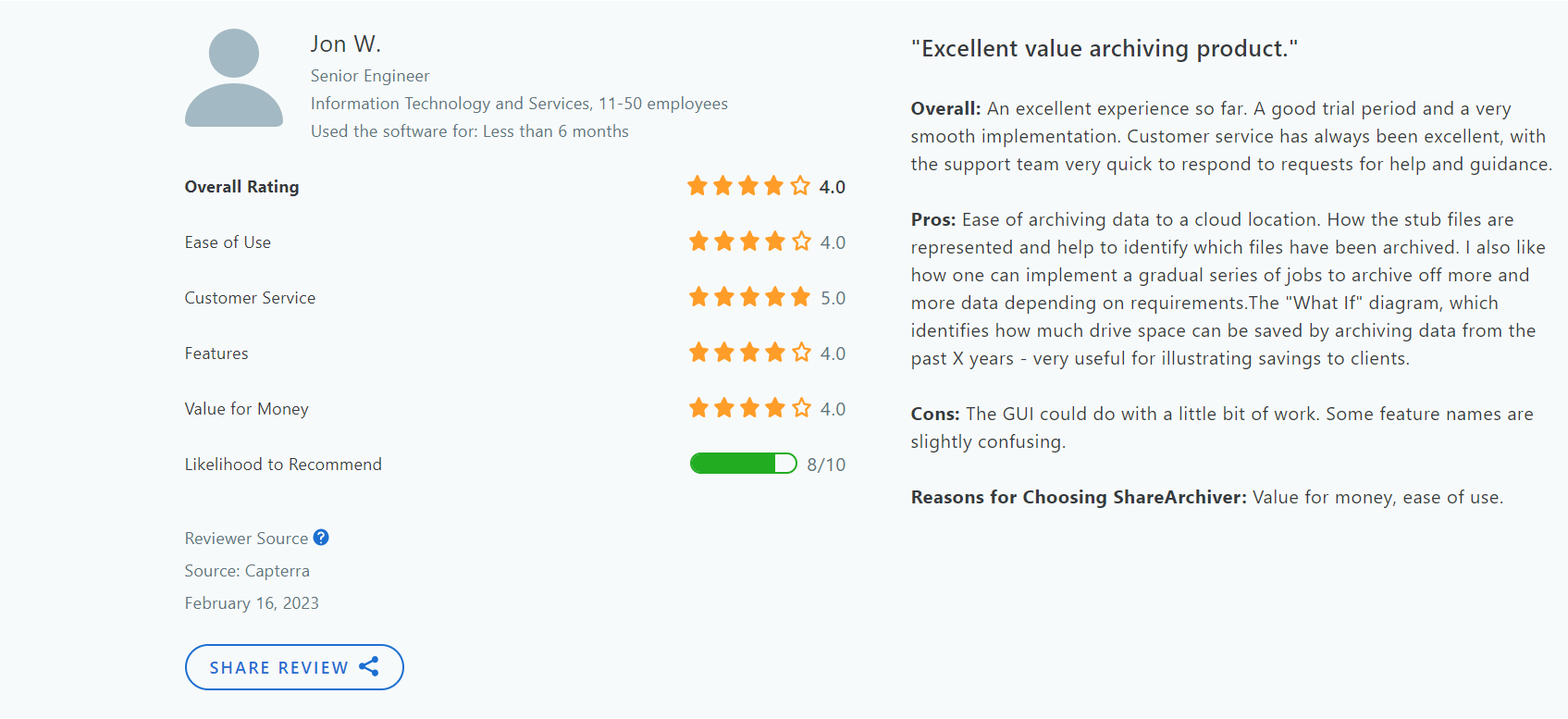
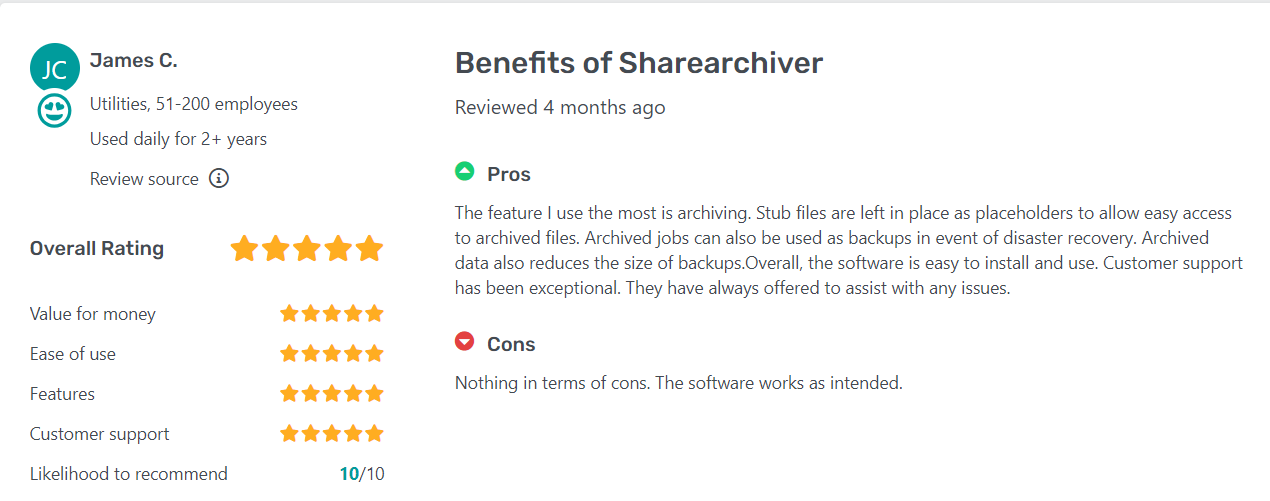
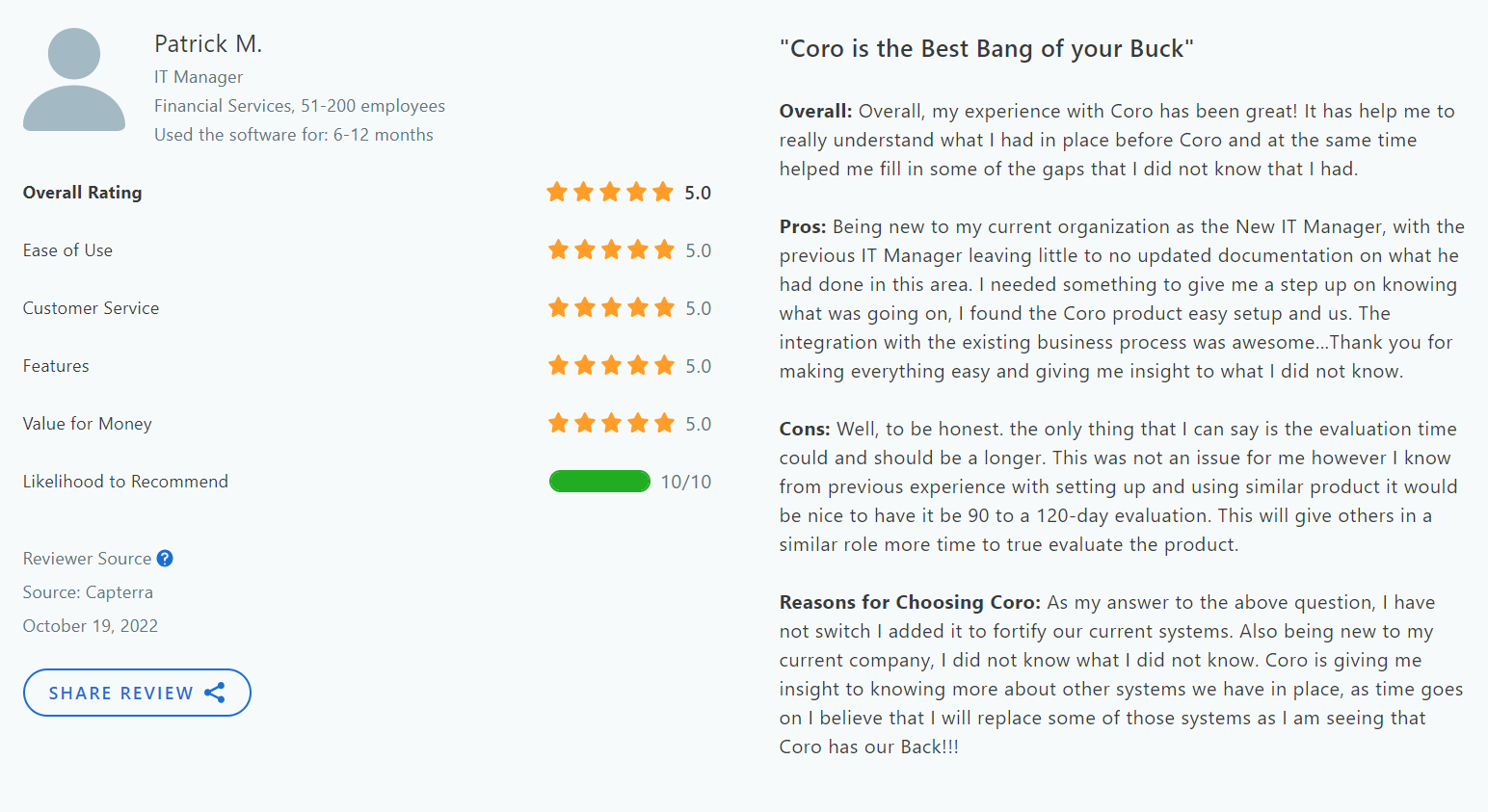
Testimonials/Reviews
Here’s what real users have to say about ShareArchiver:
The Bottom Line
ShareArchiver stands out for its top-tier security controls and comprehensive data management capabilities in line with compliance standards, making it a stellar choice for small businesses concerned about data security
2. Tenable Cloud Security (Nessus)
Tenable Cloud Security is a cloud service provider that has been offering a unified, risk-based IT/OT security platform and other security responsibilities for the past 40 years.
It has established itself as a market leader.
List of Features
- Consistent Policy Enforcement
- 360 Degree View of Cloud Assets
- Audit and Compliance Reporting
- Vulnerability Management
- Threat Detection
- Predictive Prioritization
- Web Application Scanning
- Container Security
- Operational Technology Security
- Integrated Risk Management
Top 3 Features
1. Consistent Policy Enforcement
Tenable Cloud Security’s consistent policy enforcement feature provides a unified framework for managing and enforcing security policies across all cloud computing environments.
This feature is invaluable as it ensures security standards are uniformly applied, reducing the likelihood of data breaches due to inconsistent policies or security gaps.
This also streamlines policy management.
2. 360 Degree View of Cloud Assets
This feature provides a comprehensive, holistic view of all your cloud assets.
It allows businesses to monitor all their cloud-based resources in one place and mitigate any cloud security risks before they amplify.
This comprehensive view aids in quickly identifying potential vulnerabilities, ensuring that necessary security measures can be implemented promptly.
Without such a view, businesses could risk overlooking certain assets, leaving them vulnerable to attacks.
Prompt action against threats to cloud-based data assets is the key to business continuity and is a signature feature of any reliable cloud data security provider.
3. Audit and Compliance Reporting
This feature streamlines the process of audit and compliance reporting within cloud-based environments.
With an automated generation of detailed reports, this feature makes demonstrating compliance with various data security regulations easier, reducing the risk of non-compliance penalties.
In an era where regulatory requirements are becoming increasingly stringent, such a feature is indispensable.
Pros
- Useful in finding vulnerabilities in networks assets.
- Good customer support
- Easy to use
- Satisfactory reporting and feedback capabilities
Cons
- The vulnerability scanner produces inaccurate results at times
- Costly professional version makes it impractical for small businesses
- The Pro version is limited to a single user only
Pricing
Tenable offers a free demo for users before buying. It has tailored plans according to the needs of clients.
Customer Support
- Knowledge base
- Chat
- FAQs
- Forums
- Help desk
- Phone support
Available Platform Support
- Windows
- MacOS
Average Ratings
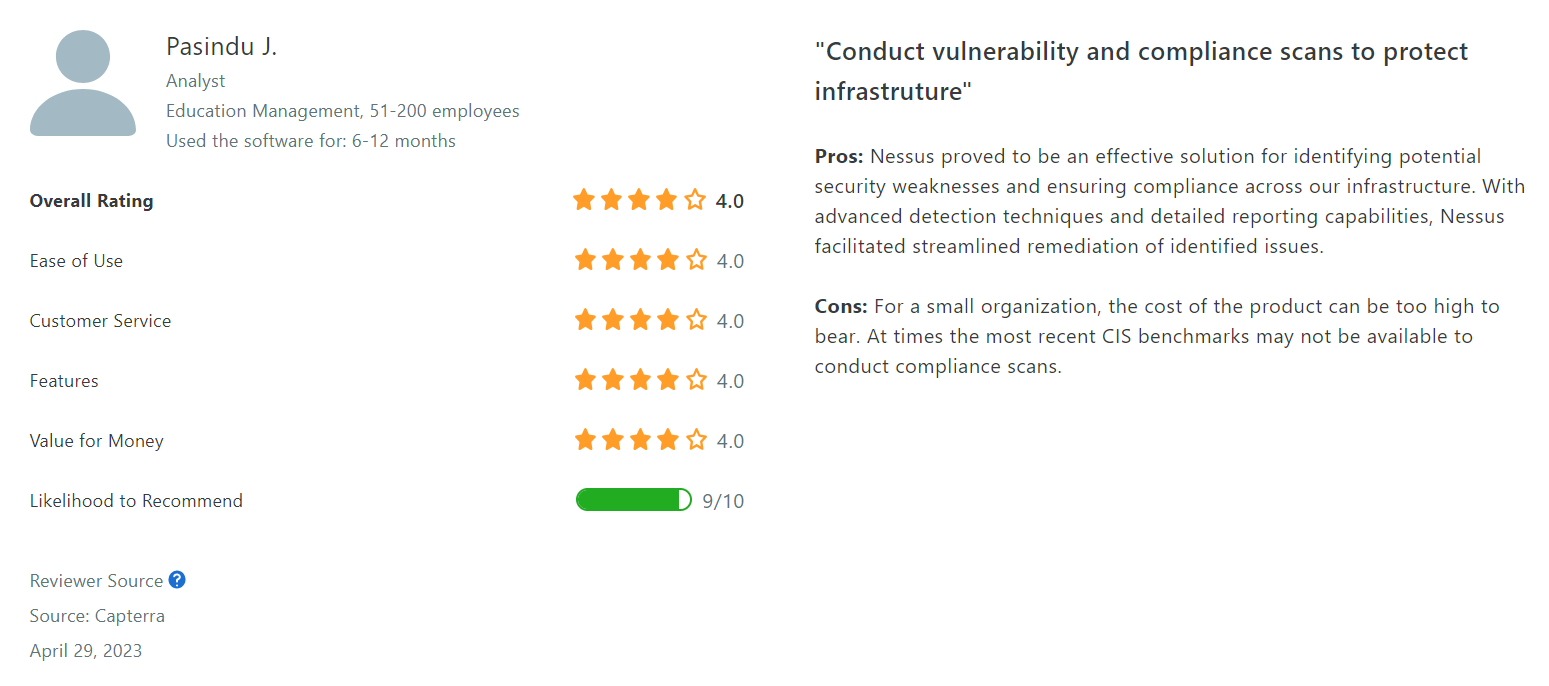
Tenable Nessus ranks at 4.5 on G2 and 4.7 on Capterra and GetApp.
Testimonials/Reviews
Here are some reviews by users who have tried Tenable Cloud Security:
The Bottom Line
Tenable Cloud Security provides a robust, comprehensive solution, making it an excellent choice for businesses with diverse cloud assets.
Although its services and scope are not as useful for small businesses as expected, it works perfectly for large organizations.
3. Acronis Cyber Protect Cloud
Acronis Cyber Protect Cloud is a unified cloud data protection solution that integrates backup, disaster recovery, AI-based malware, and ransomware protection.
The software utilizes innovative AI technology to provide cutting-the-edge data security solutions to users.
List of Features
- Advanced security + EDR
- Email Security
- Data Loss Prevention
- AI-based Protection
- Anti-Ransomware
- Full Disk-Image Backup
- File Sync and Share
- Remote Management
- Notary and ASign
- Secure VPN Connectivity
Top 3 Features
1. Advanced security + EDR
Acronis Cyber Protect Cloud features an advanced security solution with Endpoint Detection and Response (EDR).
This feature rapidly detects, analyzes, and remediates advanced cyber threats targeting endpoint devices.
It uses Artificial Intelligence and machine learning algorithms to identify malicious activities, making it easier to prevent breaches.
2. Email Security
Acronis Cyber Protect Cloud offers robust email security features, protecting businesses’ communication channels from threats such as phishing, spam, and malware.
This feature scrutinizes incoming emails for suspicious content, attachments, or links, ensuring that only safe and relevant emails reach your inbox.
Given the prevalence of email as an attack vector, robust email security is crucial.
3. Data Loss Prevention
This feature helps businesses prevent unintentional or accidental data loss, preserving the integrity and availability of data.
It includes functionalities such as data backup, secure data transmission, and access control, which all work together to prevent data loss scenarios.
This is vital as data loss can result in substantial business disruptions and financial loss.
Pros
- Easy to setup
- Reliable for offsite backups
- Proactive endpoint and ransomware protections
- Usage space-based pricing
Cons
- Dissatisfactory customer support
- Lack of much-needed integrations
- Limited self-troubleshooting capabilities
Pricing
Acronis offers a 15-day trial before users can sign up for the service. Later, they can contact sales for a tailored price plan.
Customer Support
- Chat
- FAQs
- Forums
- Help desk
- Knowledge base
- Phone support
Available Platform Support
- Windows
- MacOS
- Android
- iOS
Average Ratings
Acronis Cyber Protect Cloud ranks at 4.7 on G2. However, Capterra and GetApp rank it at 4.1.
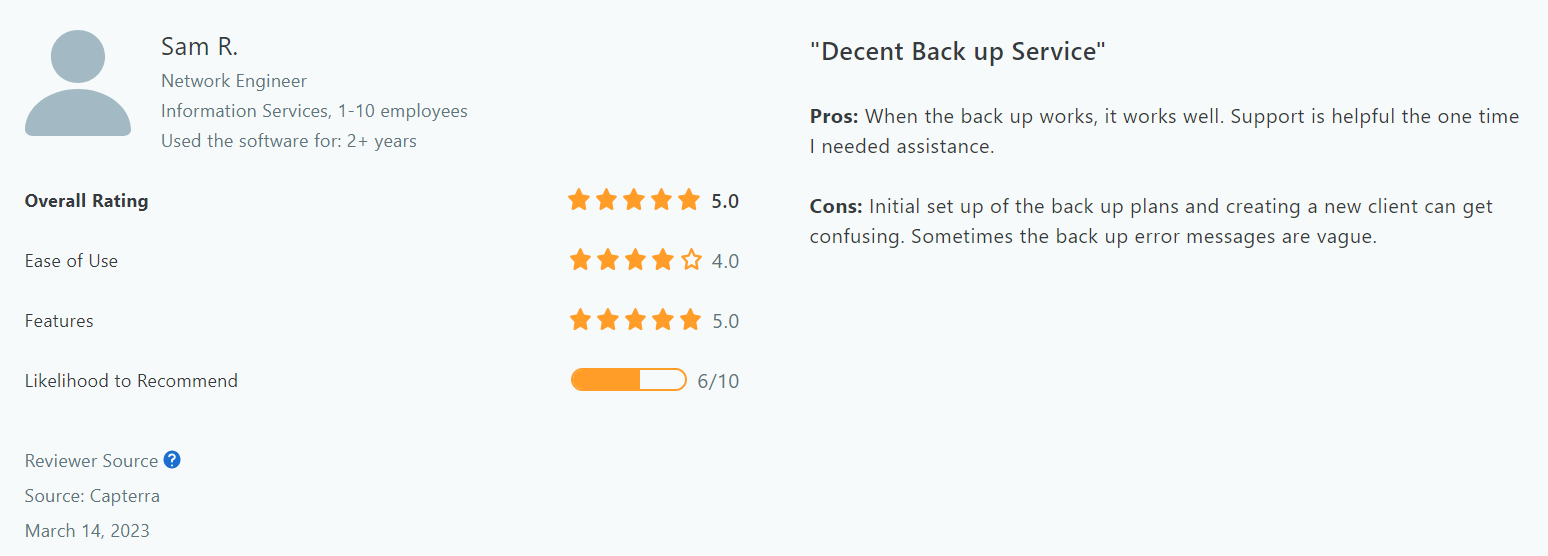
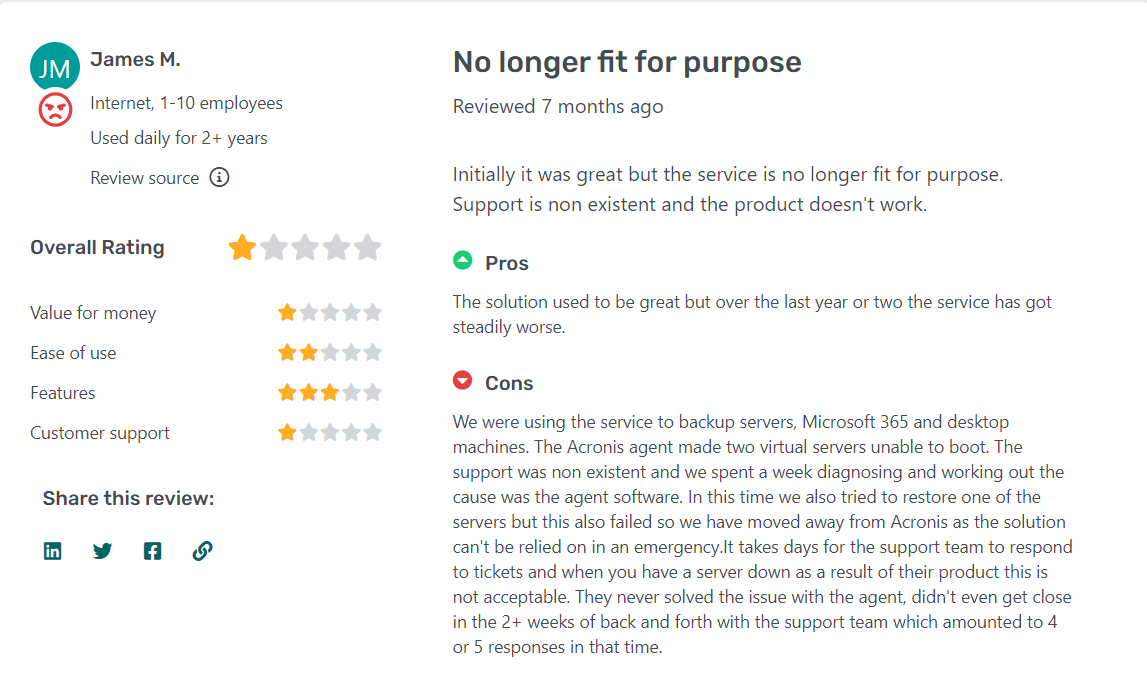
Testimonials/Reviews
Here are some user reviews for Acronis Cyber Protect Cloud:
The Bottom Line
Acronis Cyber Protect Cloud is a comprehensive solution for businesses seeking advanced threat protection with a wide array of features covering all aspects of security.
Its diverse price plans allow potential users to choose their preferred plan and start their services.
4. Druva Data Resiliency Cloud
Established in 2008, Druva offers data management and protection for the cloud era, focusing on data backup and recovery.
The data security provider claims to help users reduce overall service costs by 50%.
We shall analyze its features to see how well the software matches this claim.
List of Features
- Data Archiving
- Backup and Recovery
- Disaster Recovery
- Ransomware Protection
- Proactive Compliance
- Auto-tiering
- Federated Search
- Anomaly Detection
- Legal Hold Management
- Storage Optimization
Top 3 Features
1. Data Archiving
Druva’s data archiving feature securely retains business data over long periods, even inactivity.
This ensures that all data, including old and infrequently accessed files, are securely stored and can be accessed as and when required.
This feature is critical for businesses for historical analysis, compliance purposes, or recovery from data loss incidents.
2. Backup and Recovery
This feature ensures that data is backed up regularly and can be restored quickly during data loss.
Regularly creating copies of data and storing them in secure locations reduces the risk of data loss due to incidents like cyberattacks or system failures.
The recovery aspect ensures businesses can restore their operations quickly after a data loss incident, minimizing downtime.
3. Disaster Recovery
Disaster recovery is a strategic approach that allows businesses to recover critical functions after catastrophic events, such as natural disasters or cyberattacks.
This feature involves preparing recovery strategies, tools, and procedures to ensure minimal impact on business operations.
In the face of increasing cybersecurity threats and unforeseen disasters, having a robust disaster recovery plan is essential.
Pros
- Efficient data backup and recovery
- Easy to set up and use
- Good cloud protection capabilities
Cons
- Frequent crashes
- System inabilities to mitigate crashes effectively
Pricing
Druva offers a free trial and demo version. However, users must contact sales to get their software quotes.
Customer Support
- Chat
- Help desk
Available Platform Support
- Windows
- MacOS
Average Ratings
Druva ranks at 4.7 at GetApp and Capterra. However, G2 ranks it at 4.6.
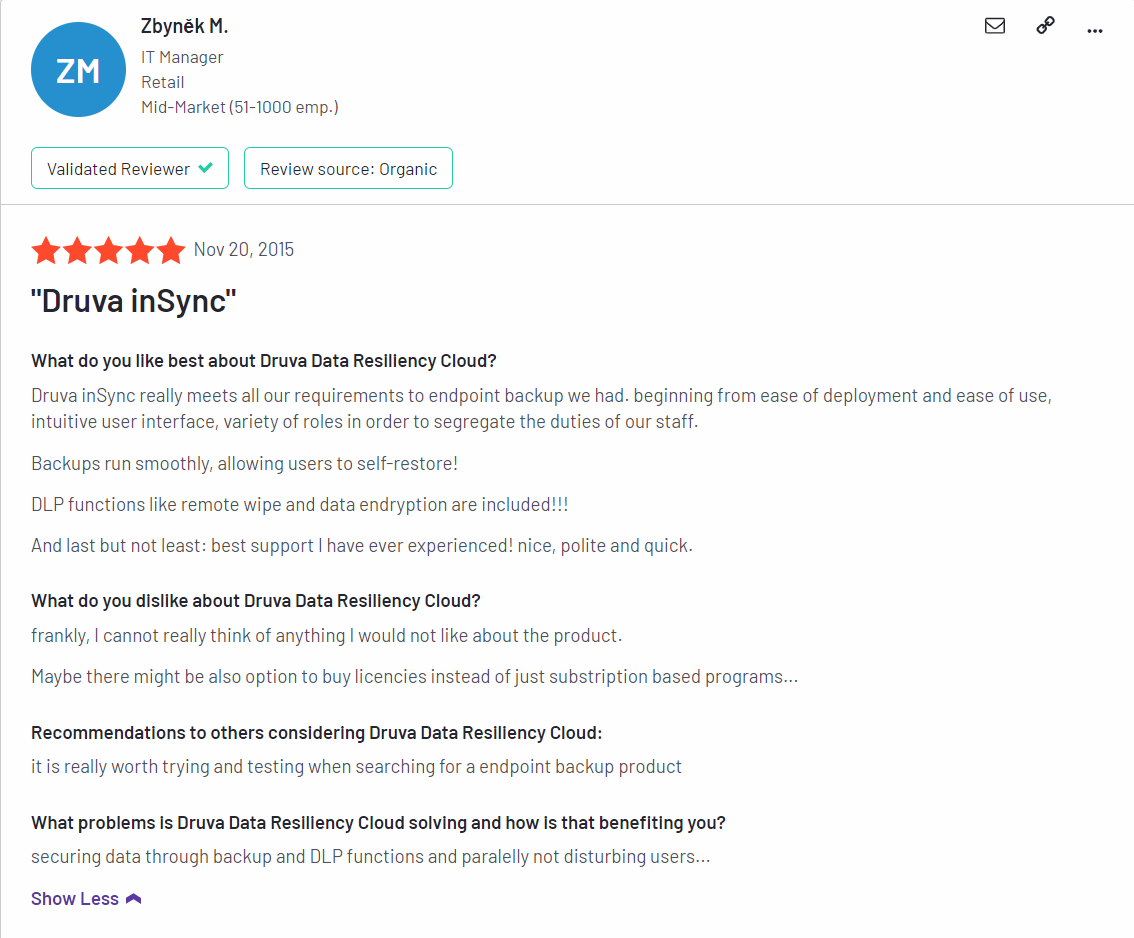
Testimonials/Reviews
Here are some of the reviews users have shared about their experience using Druva:
The Bottom
Line Druva Data Resiliency Cloud excels at data backup and recovery, providing small businesses with robust data resiliency solutions. Although the developers can better manage the memory it uses, current users are satisfied with its features.
5. Trend Micro Hybrid Cloud Security
Established in 1988, Trend Micro Hybrid Cloud Security has been at the forefront of cybersecurity.
Its Hybrid Cloud Security offers an all-inclusive, automated security solution designed to provide robust and consistent protection across the cloud environment, including physical, virtual, and cloud workloads.
List of Features
- Cloud Security
- File Storage Security
- Endpoint and Email Security
- Virtual Network Protection
- Data Loss Prevention
- Intrusion Prevention
- Anti-Malware Web Reputation
- Services Log Inspection
- Application Control
Top 3 Features
1. Cloud Security
The Cloud Security feature provides a comprehensive shield that defends your cloud infrastructure from multiple threats, including data breaches, identity theft, and malware attacks.
With the massive increase in cloud adoption, safeguarding your cloud infrastructure from these pervasive threats is more crucial than ever.
Trend Micro Hybrid Cloud Security achieves this through constant monitoring, threat detection, and automated responses.
2. File Storage Security
File Storage Security plays a crucial role in protecting your data at rest.
It employs sophisticated security measures like encryption and access controls to make sure that only authorized personnel access your business-critical data.
Trend Micro Hybrid Cloud Security’s File Storage Security seamlessly integrates with your cloud storage solution, adding an extra layer of security.
3. Endpoint and Email Security
This feature offers comprehensive protection for all devices accessing your network (endpoints) and your email system, two major points of vulnerability.
The feature scans for potential threats like malware or phishing attempts in real time, ensuring secure communication and data flow across your organization.
Pros
- Advanced protection
- User-friendly services
- Satisfactory technical support
Cons
- It can be overwhelming for small businesses without IT staff
- Causes lags in systems during antivirus scans
Pricing
Trend Micro offers a 30-day trial for its software. For full pricing information, customers can contact their sales department.
Customer Support
- Chat
- Knowledge base
- 27/7 live rep
- Phone support
- FAQs
- Forums
- Help desk
Available Platform Support
- Windows
- MacOS
Average Ratings
Trend Micro Hybrid Cloud ranks at 4.6, according to G2.
Testimonials/Reviews
Here are some user reviews regarding their experience with Trend Micro Hybrid Cloud:
The Bottom Line
Trend Micro Hybrid Cloud Security provides a comprehensive, automated security solution for your cloud environment.
Its extensive feature set and advanced protection techniques make it a top preference for businesses of all sizes.
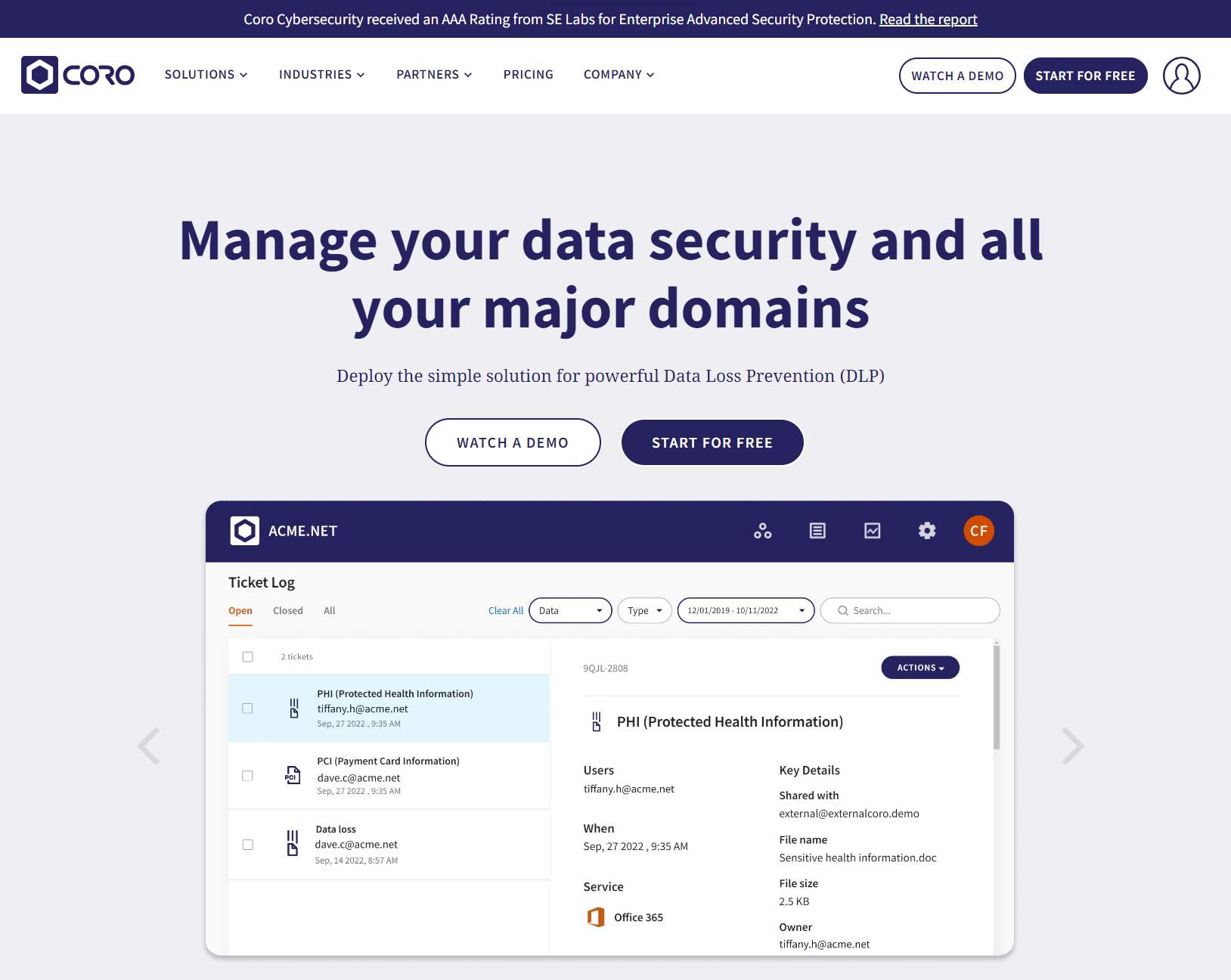
6. Coro Cybersecurity
Coro Cybersecurity offers a robust, all-in-one security solution, automating the detection and remediation to ensure fast, efficient response to potential threats.
The company was formed to provide non-disruptive security within an affordable price range, working like a productivity solution for security.
List of Features
- All-in-one Security Solution
- Automatic Detection and Remediation
- Data Leak Protection
- Threat Intelligence
- Endpoint Protection
- Network Security
- Email Security
- Web Security
- Mobile Device Security
- Incident Response
Top 3 Features
1. All-in-one Security Solution
With an ever-expanding digital threat landscape, businesses need a holistic security solution that covers all bases.
Coro Cybersecurity’s All-in-one Security Solution offers a single platform that protects networks, endpoints, emails, and more.
It reduces the need for multiple security solutions, simplifying management and potentially saving costs.
2. Automatic Detection and Remediation
A quick response to threats can differ between a minor incident and a major breach.
Coro’s Automatic Detection and Remediation feature uses advanced algorithms to detect potential threats as soon as they appear and instantly takes steps to neutralize them, thus significantly reducing the risk of data breaches.
3. Data Leak Protection
Data leaks can cause irreparable and considerable damage to a business’s reputation.
Coro’s Data Leak Protection monitors and controls data movement across the network, preventing unauthorized access, transmitting sensitive information, and ensuring your critical business data remains secure.
Pros
- Effective cloud and endpoint protection services
- Easy to use
- Good customer support
- Provides additional layers of protection and alerts
- Network connection monitoring
Cons
- Phishing emails slip under the radar
- Users cannot whitelist suspected emails manually
- Cannot prevent DLP emails from being sent out
Pricing
- Coro offers a free version
- Monthly Plans:
- Coro Flexible + Cyber Advisor: $11.99 per user per month
- Yearly Plans:
- Coro Flexible + Cyber Advisor: $8.99 per user per month, billed annually.
- Coro Edge: $12.99 per user per month, billed annually.
Customer Support
- Chat
- FAQs
- Forums
- Help desk
- Phone support
- 24/7 live rep
Available Platform Support
- Windows
- Mac OS
Average Ratings
GetApp and Capterra rate Coro Cybersecurity at 4.6 while G2 rates it at 4.7.
Testimonials/Reviews
Here are some reviews shared by users on software review platforms:
The Bottom Line
Coro Cybersecurity offers a comprehensive, automated security solution.
Its all-in-one approach simplifies security management while ensuring efficient detection and remediation of threats.
7. Zscaler Cloud Platform
Zscaler Cloud Platform provides comprehensive internet and web security solutions encapsulating users, devices, applications, and services.
List of Features
- IoT and OT Security Systems
- Workload Security
- Zero Trust App Access
- Data Loss Prevention
- Advanced Threat Protection
- Secure Access
- Service Edge (SASE) SSL Inspection
- DNS Layer Enforcement
- Cloud Firewall
- Bandwidth Control
Top 3 Features
1. IoT and OT Security System
With more devices connected to the internet, securing IoT and OT systems is increasingly important.
Zscaler’s IoT and OT Security System protects these systems from external threats and unauthorized access.
The feature uses real-time threat intelligence and automated responses to keep your IoT and OT infrastructure secure.
2. Workload Security
Workload Security protects your cloud-based workloads from threats like unauthorized access and malware.
Zscaler’s Workload Security feature continuously monitors and controls access to your workloads, ensuring that only authorized users can access your critical applications and data.
3. Zero Trust App Access
Based on the principle of “never trust, always verify,” Zero Trust App Access enhances security by ensuring that only authorized users can access specific applications.
This minimizes the risk of inside threats, effectively reducing the attack surface.
Pros
- Provides seamless and convenient operations
- Integrations with other tools and software for better data protection
- Provides suitable security for basic computing
Cons
- Difficulty in setting exceptions
- Users complain of inefficient support
- Frequent issues with the system leave users frustrated
Pricing
Zscaler offers different packages that cater to different needs of clients.
Business, Transformation, and Unlimited are three plans users can avail of.
However, they have to contact the sales department for tailored solutions.
Customer Support
Zscaler offers 24/7 live rep for users.
Available Platform Support
- Windows
- MacOS
Average Ratings
Zscaler is rated 4.7 on G2. However, Capterra and GetApp rate it to 4.3 only.
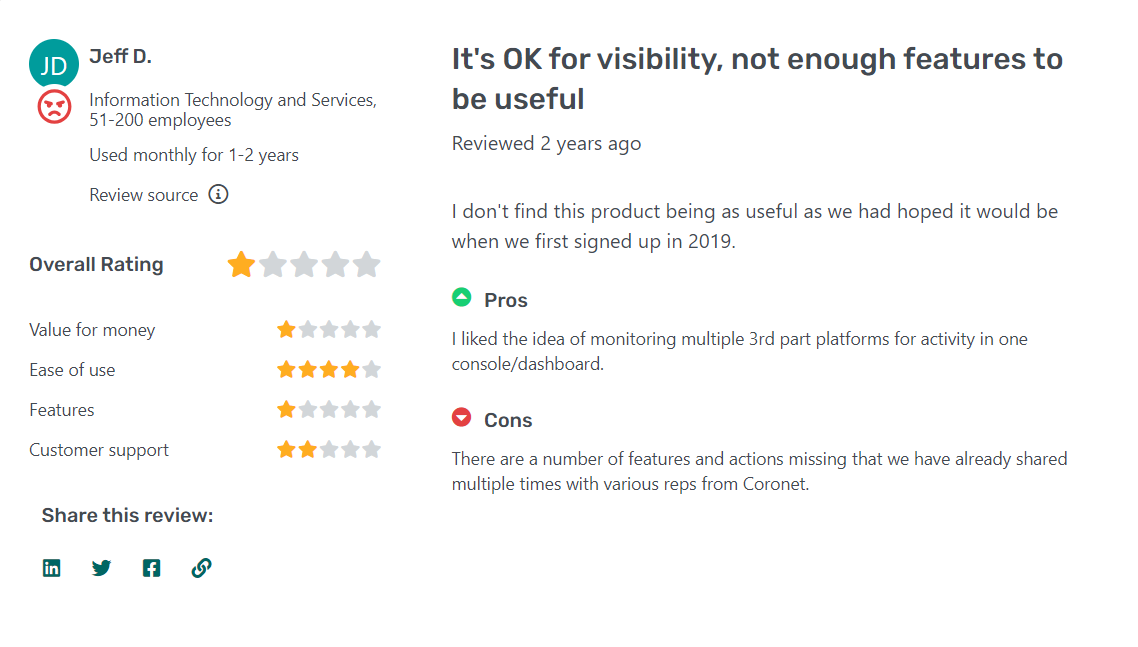
Testimonials/Reviews
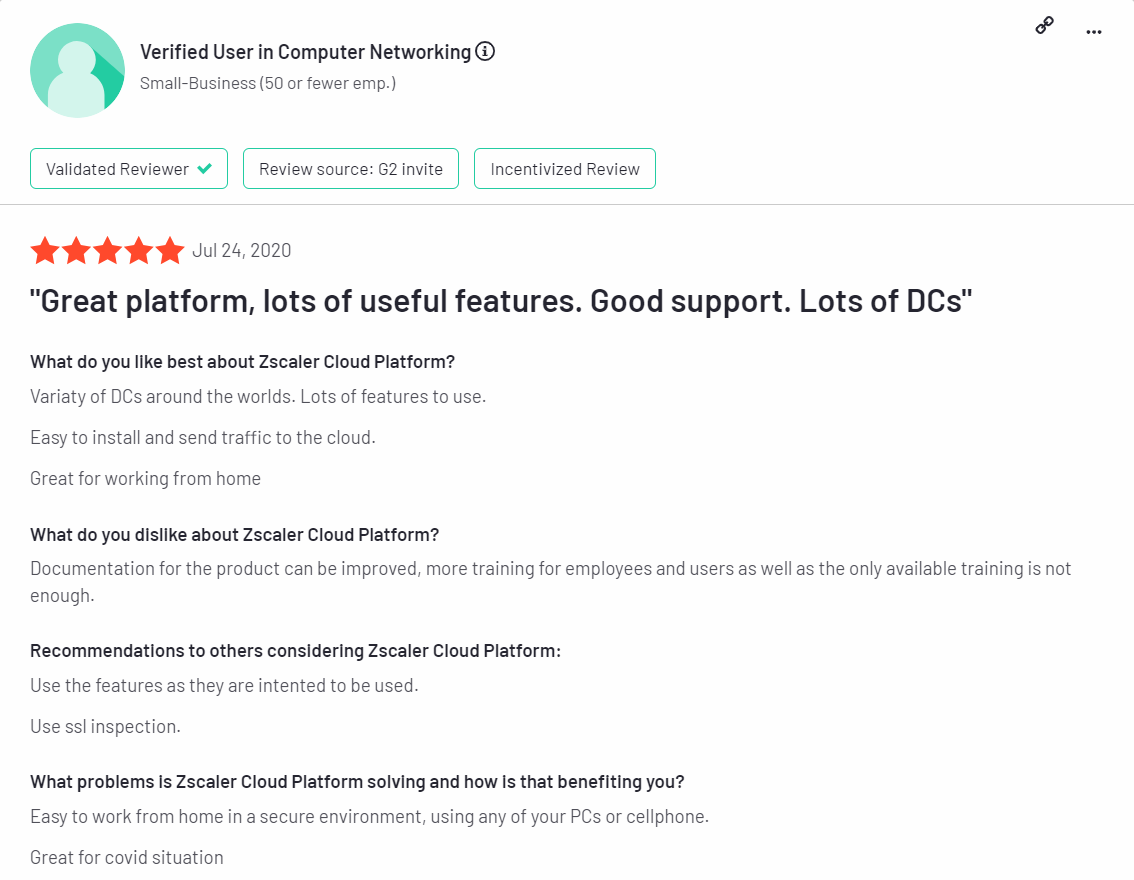
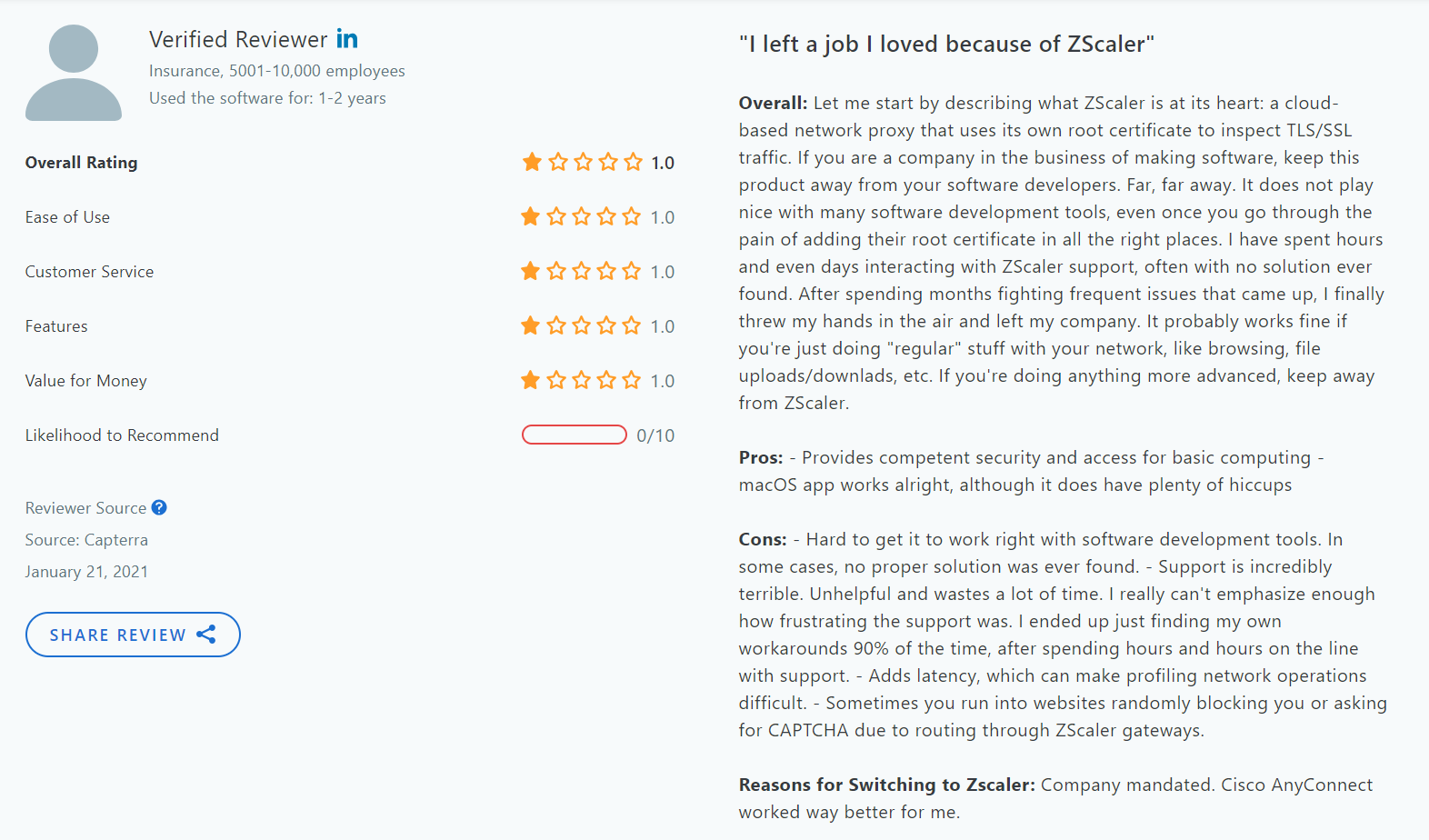
Here is what real users have to say about Zscaler’s use experience:
The Bottom Line
Zscaler Cloud Platform provides robust internet and web security solutions, protecting your users, devices, applications, and services from various threats.
8. CloudGuard Network Security (IaaS)
CloudGuard Network Security (IaaS) by Check Point is a comprehensive solution that provides advanced threat prevention to keep your data and assets in the cloud secure.
List of Features
- Secure Cloud Deployment
- Cloud Network Security
- Threat Prevention
- Segmentation Identity
- Awareness VPN
- Intrusion Prevention System (IPS)
- Antivirus Anti-Bot
- Data Loss Prevention
Top 3 Features
1. Secure Cloud Deployment
CloudGuard’s Secure Cloud Deployment feature safeguards your data and applications during the migration to the cloud and once hosted.
This feature ensures the cloud environment is secure, protecting your business from potential threats during the sensitive transition phase.
2. Cloud Network Security
Cloud Network Security safeguards your cloud-based networks from threats such as unauthorized access and data breaches.
This feature of CloudGuard monitors network traffic for potential threats and takes immediate action to mitigate them, ensuring the integrity and security of your cloud-based networks.
3. Threat Prevention
CloudGuard Network Security employs advanced threat prevention techniques to protect your data and applications from malware, phishing, and ransomware.
This feature uses real-time threat intelligence, continuous scanning, and automated remediation to secure your cloud infrastructure.
Pros
- Cyberattack intelligence in advance
- Automated networking services
- Exceptional threat detection
Cons
- Expensive as compared to other solutions providing the same services
- Users need more time to familiarize themselves with the interface and usage
Pricing
Interested clients can get an exclusive price quote for their required services from the sales department.
Customer Support
- Chat
- 24/7 live rep
- Knowledge base
- Phone
Available Platform Support
- Windows
- MacOS
Average Ratings
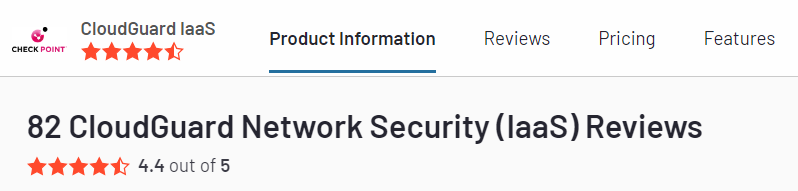
CloudGuard ranks at 4.4 on G2.
Testimonials/Reviews
Here’s what users have expressed about their experience with CloudGuard:
The Bottom Line
CloudGuard Network Security (IaaS) provides robust cloud security solutions, ensuring the safety of your cloud deployment, network, and data.
Its advanced threat prevention features make it an excellent choice for businesses looking for comprehensive cloud security.
9. Immuta
Immuta, established in 2015, is a data management platform for data science, offering a cloud-native solution that provides scalable, secure, and compliant access to organizational data.
List of Features
- Data Leakage Prevention
- Secure Data Access
- Zero Trust Enablement
- Dynamic Data Masking
- Policy-Based Data Governance
- Automated Data Cataloging
- Sensitive Data Detection
- Data Source Integration
- Granular Auditing Access Control
Top 3 Features
1. Data Leakage Prevention
Data leakage poses a significant risk to businesses.
If sensitive information falls into the wrong hands, it could lead to reputation damage, regulatory fines, or loss of intellectual property.
Immuta’s data leakage prevention feature employs advanced mechanisms to detect potential leakage paths and stop data leakage in its tracks.
This feature monitors and controls data transfer between different points in the network, ensuring the confidentiality and integrity of sensitive information are maintained.
2. Secure Data Access
Unauthorized access to data is a prevalent concern among businesses.
Immuta’s secure data access feature leverages advanced access control mechanisms to ensure that only authorized users can access specific data, depending on their access rights and privileges.
This feature is powered by a robust permission system that uses user and data classification to determine access.
It also incorporates the principles of the least privilege and need-to-know to minimize the exposure of sensitive data
3. Enabled Zero Trust
As part of its comprehensive security framework, Immuta has implemented Zero Trust principles.
Zero trust is a security concept requiring all users, even those inside the organization’s network, to be authorized, authenticated, and consistently validated for security configuration before being granted access to applications and data.
This strategy mitigates the risk of insider threats, reduces the attack surface, and improves data and system security.
Pros
- Intuitive and user-friendly interface
- Provides adaptive and scalable solutions according to individual needs
- Seamless integration with other necessary tools
- Easy to create or remove user access
Cons
- Gaps in customer services and support
- Problems with troubleshooting
- Pricing plans need improvement
Pricing
Like other cloud data security solutions, Immuta’s prices are tailored to users’ needs. Interested clients can request a demo and contact with sales representatives for a detailed price plan.
Customer Support
- FAQs
Available Platform Support
- Windows
- MacOs
Average Ratings
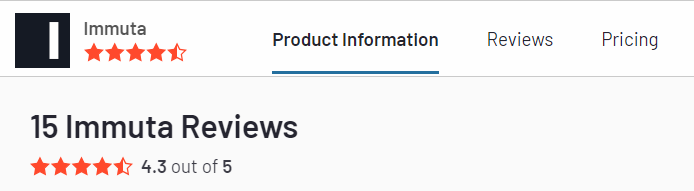
G2 rates Immuta at 4.3.
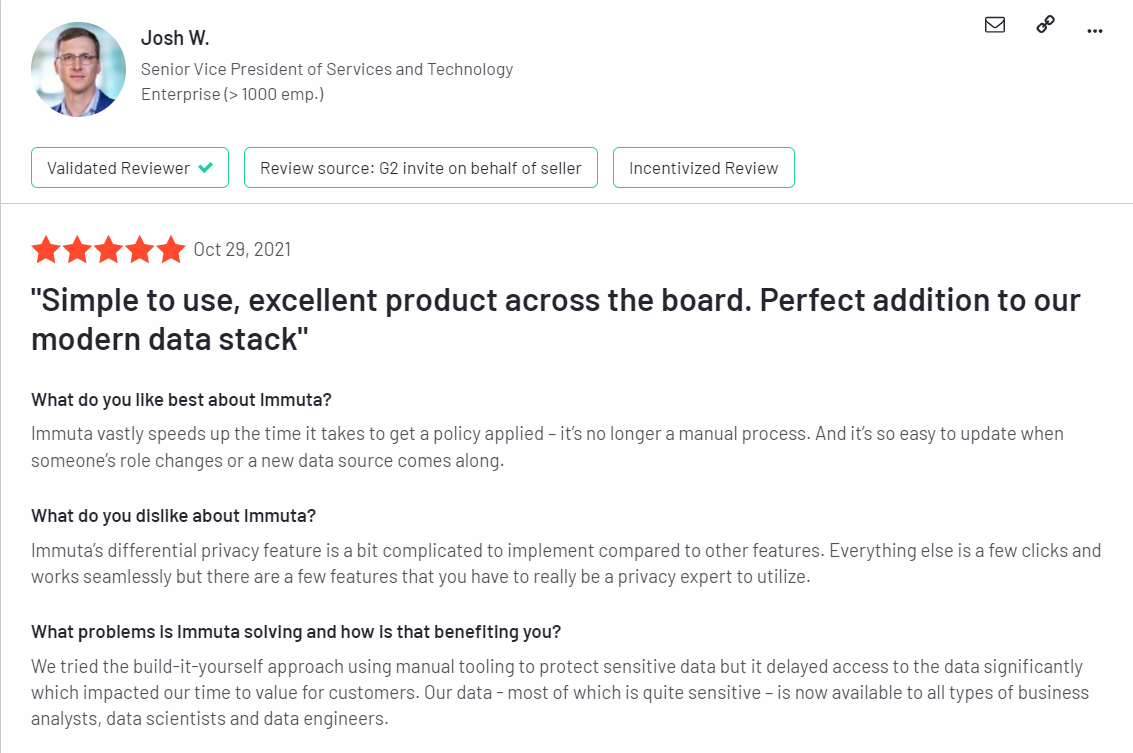
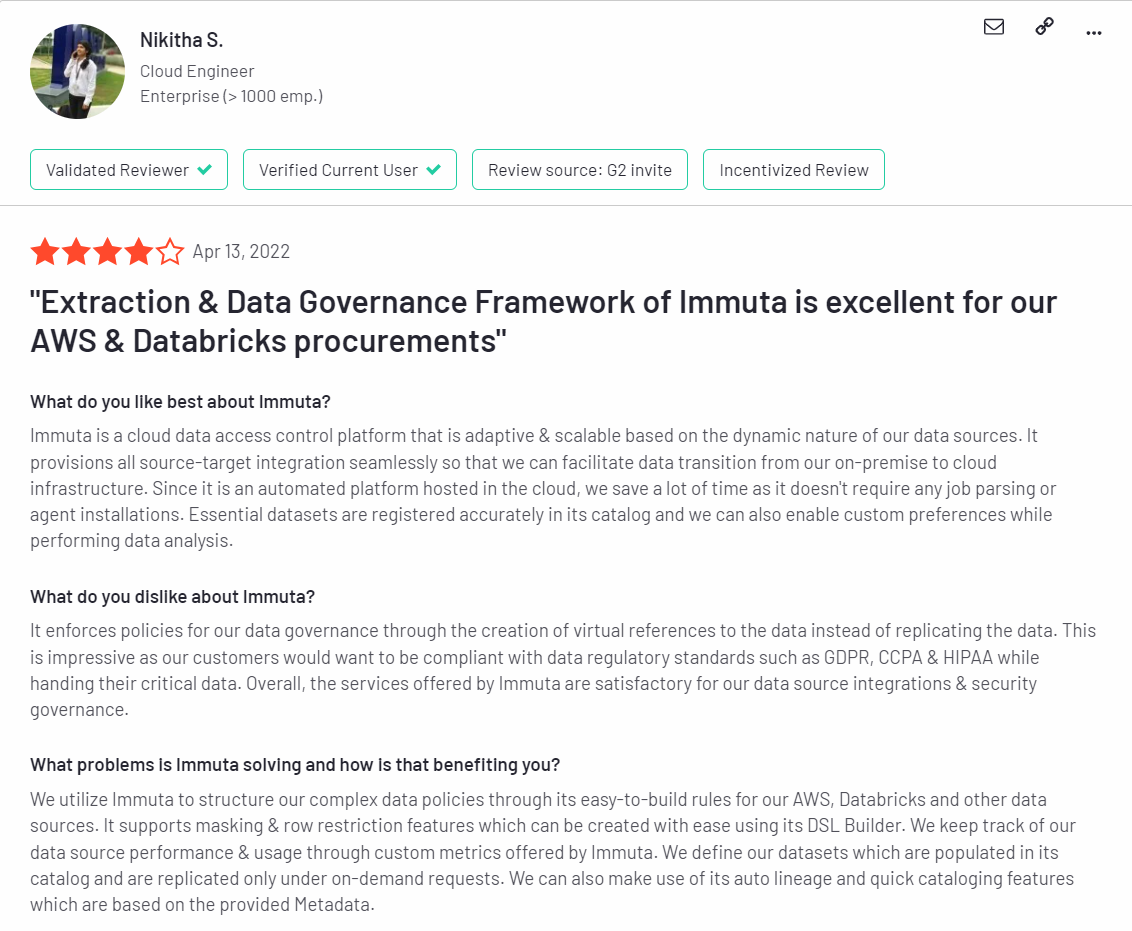
Testimonials/Reviews
Here are some user reviews shared on G2:
The Bottom Line
Immuta’s strong focus on data governance and secure data access, along with its commitment to the Zero Trust security model, makes it a robust solution for companies seeking to improve their data security and compliance.
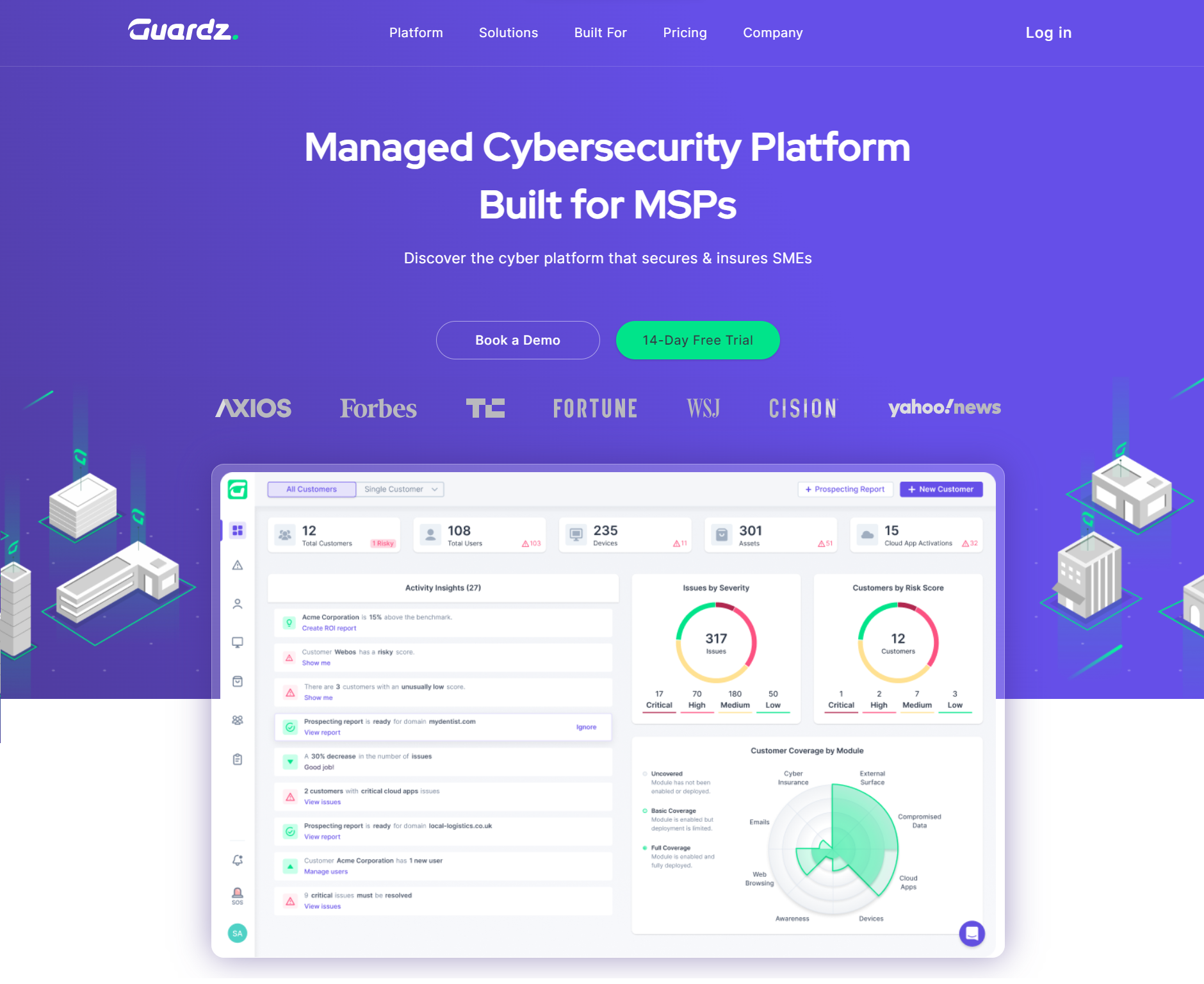
10. Guardz
Guardz is a cloud-based security software known for its multifaceted protection against digital threats.
Its broad range of security capabilities helps small businesses protect their assets seamlessly.
List of Features
- Phishing Protection
- Anti-Ransomware
- Data Loss Prevention
- Real-time Threat Detection
- Malware Protection
- Secure Browsing
- Email Security
- Firewall Integration
- Advanced AI Detection
- Endpoint Security
Top 3 Features
1. Phishing Protection
Phishing attacks, where attackers masquerade as a reputable entity to trick individuals into providing sensitive data, are a growing threat in today’s digital landscape.
Guardz’s phishing protection feature uses advanced detection techniques to identify phishing attempts in real time.
This mechanism works by analyzing incoming emails and websites’ metadata and content for signs of phishing.
It then alerts users about potential threats, preventing them from falling victim to attacks.
2. Anti-Ransomware
In a ransomware attack, cybercriminals use malicious software to block access to a computer system until some money is paid.
Guardz’s anti-ransomware feature works by identifying the unique behavior of ransomware through heuristic analysis.
The software continuously scans the system to detect changes or activities resembling ransomware operations.
Once detected, Guardz immediately isolates the affected system and removes the ransomware, ensuring data integrity and system uptime.
3. Data Loss Prevention
Guardz’s data loss prevention feature aims to ensure that sensitive data does not leave the corporate network, whether that data is at rest, in use, or transit.
It uses a combination of policies, rules, and regulations to identify and keep track of sensitive information and monitor and control data endpoints, networks, cloud storage, and user activities.
The system alerts administrators to potential breaches and violations, ensuring they can quickly prevent data loss.
Pros
- Comprehensive digital threat protection.
- Real-time threat detection and response.
- Cost-effective for small businesses.
Cons
- Even though it provides scalability, the software lacks the additional customizations necessary for complex IT environments
- Initial users find the interface confusing
Pricing
Unlike other cloud data security solutions, Guardz has comparatively straightforward price plans which users can pick from. The software offers different categories for different types of clients.
- For MSPs:
- Essentials: free
- Pro: $9 per user, or $7 per user per month when billed annually.
- Master: caters to more than 500 users. Clients can contact Sales for tailored plans.
- IT Pros:
- Essential: free
- Pro: for more than 201 users. Clients can contact Sales for their price plans.
- The Business Owner package targets the needs of business owners in particular. Interested individuals can reach out to Sales department for further information.
Customer Support
- Phone
Available Platform Support
- Windows
- MacOS
Average Ratings
Guardz is rated at 4.9 on G2.
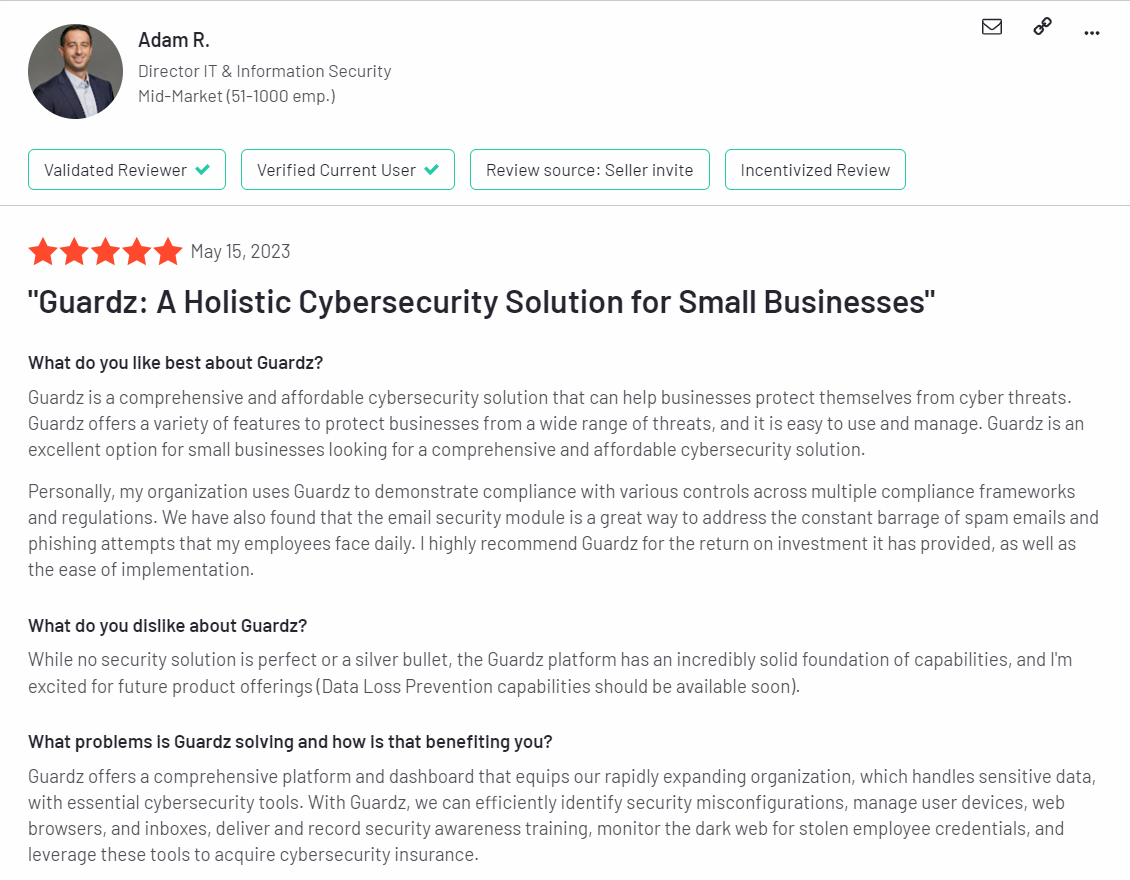
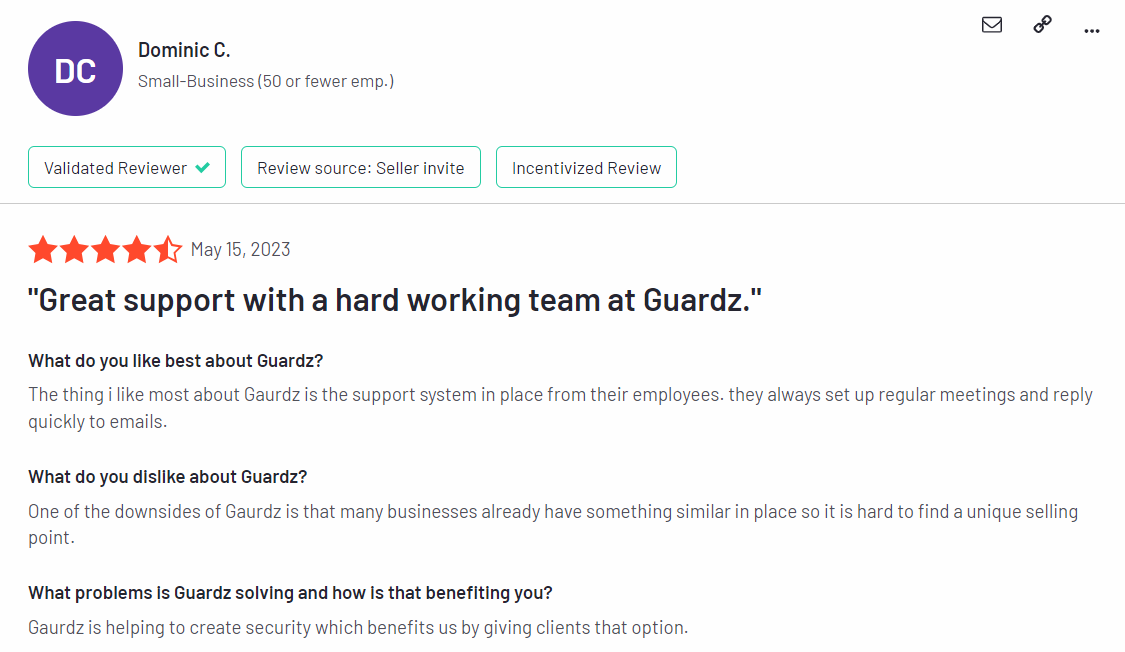
Testimonials/Reviews
Here are some of the reviews real users have left on G2:
The Bottom Line
With comprehensive threat protection features, Guardz is an excellent cost-effective solution for small businesses looking to protect their digital assets from cyber threats.
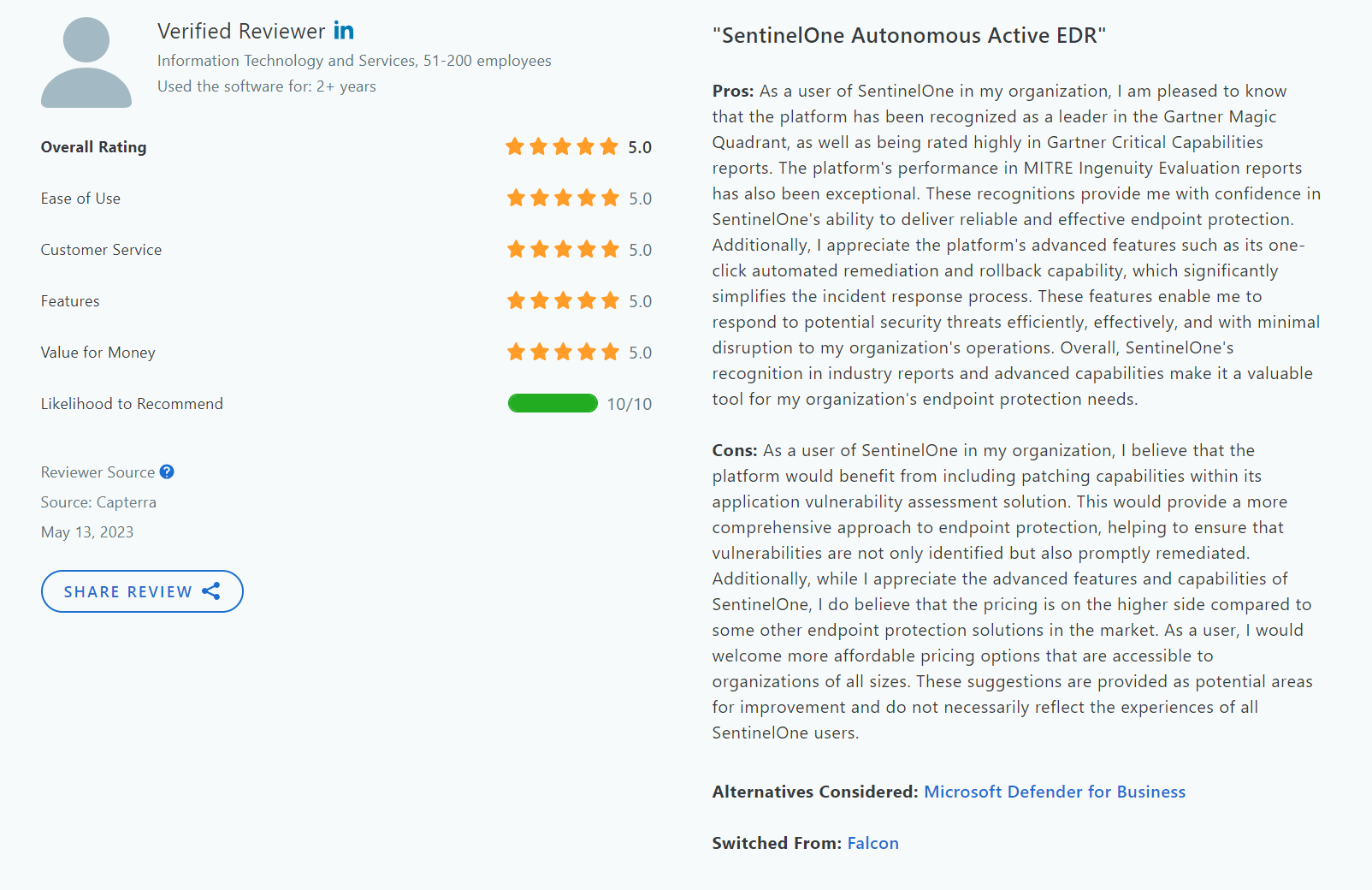
11. SentinelOne
SentinelOne is a cybersecurity software company known for its autonomous endpoint protection that detects, prevents, and responds to threats.
List of Features
- Real-Time Detection and Protection
- Instant Remediation
- Data Visibility
- Automated Threat Hunting
- Endpoint Protection
- Active Directory Protection
- Network Visibility
- Cloud Workload Protection
- Behavioral AI Technology
- Storyline Technology
Top 3 Features
1. Real-Time Detection and Protection
In the face of a rapidly evolving threat landscape, real-time threat detection and protection are crucial.
SentinelOne’s real-time detection and protection feature uses advanced AI and behavioral analysis techniques to monitor systems for any signs of malicious activity continuously.
This feature can detect even the most sophisticated and newest threats, enabling businesses to respond and remediate threats immediately before they can cause significant damage.
2. Instant Remediation
When a threat is detected, immediate action is vital to minimize its impact.
SentinelOne’s instant remediation feature quickly isolates affected endpoints, eliminating the threat from the system.
It uses artificial intelligence to automate the remediation process, reversing the changes made by the threats, such as file modifications, system configuration changes, and process alterations.
This prevents the spread of the threat and reduces the downtime caused by the incident.
3. Data Visibility
A comprehensive view of data across the network is vital for maintaining security and compliance.
SentinelOne’s data visibility feature provides complete visibility into all activities involving data across the network.
It offers insights into who is accessing the data, what data they’re accessing, when, and how.
By logging all data access and transfer activities, this feature makes it possible to detect any unauthorized or unusual data activities quickly, enhancing overall data security.
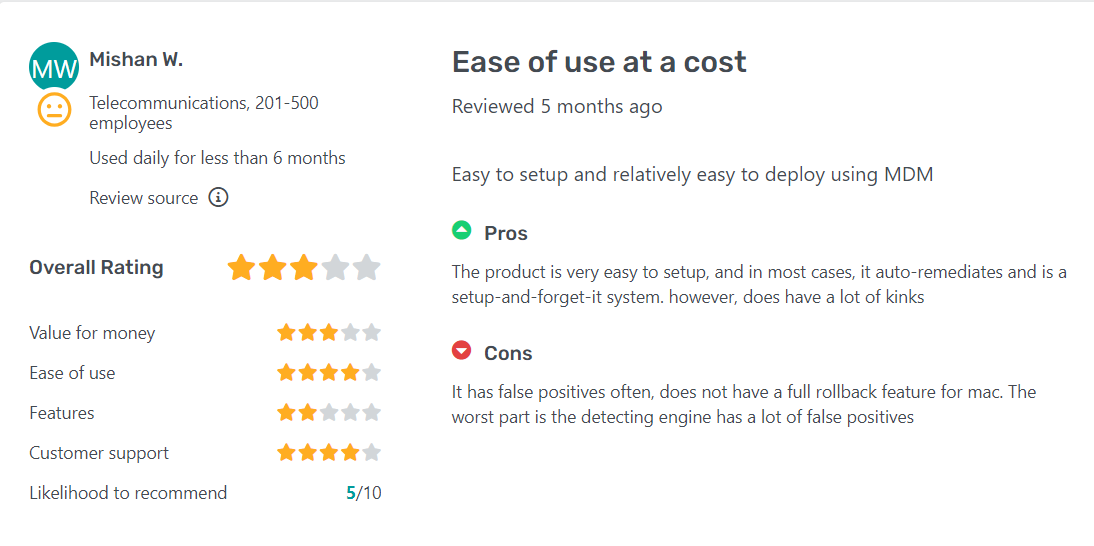
Pros
- Effective planning and implementation capabilities
- Easy to use and access
- Sophisticated threat prevention and detection
Cons
- Problems with whitelisting flagged files
- Complicated activity dashboard
- Multiple consoles confuse users
- Constant updates in user interface makes it confusing for existing users to familiarize with the new layout
Pricing
SentnelOne offers a free demo to demonstrate the software’s use and capabilities. Interested individuals can contact Sales for a full price quote.
Customer Support
- Help desk
- Knowledge base
- FAQs
- Forums
- Phone
- Chat
Available Platform
- Windows
- MacOS
Average Ratings
SentinelOne ranks at 4.3 on G2. However, GetApp and Capterra have given it quite a higher rating of 4.8.
Testimonials/Reviews
Here are some user reviews from top reviews websites:
The Bottom Line
SentinelOne is an excellent option for businesses looking for a comprehensive, AI-powered security solution with real-time threat detection and fast remediation capabilities.
12. Thales
Thales is a multinational company providing various defense, aerospace, and cybersecurity services.
Their cloud security solutions are well-regarded for their robust encryption and data protection capabilities.
List of Features
- Data Encryption
- Network Encryption
- Secure File Sharing
- Key Management
- Access Management
- Identity Verification
- Data Discovery and Classification
- Cloud Security
- Digital Signing
- High-Speed Encryption
Top 3 Features
1. Data Encryption
With data breaches on the rise, encrypting data has become a necessity for businesses.
Thales’s data encryption feature provides robust encryption for data at rest, in transit, and in use.
It uses advanced cryptographic algorithms to convert plain text data into cipher text, ensuring that it cannot be read without the decryption key even if data is intercepted.
By encrypting data, Thales helps businesses protect sensitive information, comply with regulations, and build customer trust.
2. Network Encryption
As data travels across networks, it is vulnerable to breach and unauthorized interception.
Thales’s network encryption feature protects data during transmission by encrypting it before it leaves the source, then decrypting it upon arrival at the destination.
It provides end-to-end encryption for network traffic, securing the data from potential eavesdropping and manipulation attacks.
This feature is essential in protection of sensitive information such as financial data, customer information, and intellectual property that travels across the network.
3. Secure File Sharing
In today’s collaborative work environment, secure file sharing is more important than ever.
Thales’s secure file-sharing feature ensures that files shared within or outside the organization are secure and can only be accessed by authorized individuals.
It encrypts files before they’re shared and provides decryption keys only to the intended recipients.
This feature protects the files during transmission and ensures they remain secure when stored at the recipient’s end, providing an additional layer of data security.
Pros
- Comprehensive data and network encryption capabilities.
- Secure file-sharing functionality.
- Wide range of security solutions.
Cons
- Problems with integrating with other tools and software
- Slowes down systems
Pricing
Users can contact sales for elaborate price plans.
Customer Support
- Phone
- Knowledge base
- Help desk
- Forums
- FAQs
Available Platform
- Windows
- MacOS
Average Ratings
There are not enough user ratings to rank this software.
Testimonials/Reviews
There are insufficient user reviews for Thales cloud security software.
The Bottom Line
Thales offers a wide range of robust security solutions, with particular strength in encryption.
Businesses looking for top-tier data and network encryption capabilities should consider Thales.
Comparison Table
| Data Encryption | Policy-based Access Control | Automated Data Classification | Incident Response | Data Loss Prevention | User Activity Monitoring | Data De-duplication | |
| ShareArchiver | |||||||
| Tenable Cloud Security | |||||||
| Acronis Cyber Cloud Protect | |||||||
| Druva Data Resiliency | |||||||
| Trend Micro Hybrid | |||||||
| Coro Cybersecurity | |||||||
| Zscaler Cloud Platform | |||||||
| CloudGuard | |||||||
| Immuta | |||||||
| Guardz | |||||||
| SentinelOne | |||||||
| Thales |
Best of the Best
We have shortlisted the best 12 cloud data security software for your convenience.
To make your selection of the best software even easier, we shortlist the top 3 cloud data security software that will ensure foolproof security and integrity of your data.
- ShareArchiver: It tops the list owing to its comprehensive coverage of security aspects like data encryption, incident response, and data loss prevention.
It uniquely offers policy-based access control, automated data classification, and de-duplication features. The user activity monitoring function provides an added layer of security. - CloudGuard Network Security: Coming close is CloudGuard, with robust features, including data encryption, incident response, and policy-based access control.
While it lacks data de-duplication, it excels with user activity monitoring. - SentinelOne: Sentinel One provides strong security features, including data encryption, incident response, and data loss prevention.
It’s one of the few options with automated data classification but lacks policy-based access control and data de-duplication.
Conclusion
The importance of robust cloud data security software cannot be overstated in today’s digital era.
A solution like ShareArchiver safeguards your data and offers exclusive features such as policy-based access control and automated data classification.
Its user activity monitoring capability allows an added layer of security, offering you peace of mind knowing your data is secure.
From small businesses to large enterprises, ShareArchiver is a scalable solution to your unique needs.
Don’t compromise your data security. Try ShareArchiver today, and experience the assurance of comprehensive cloud data security.
Best for Use FAQs
1. Which is the best cloud data security software for small businesses?
ShareArchiver is the perfect choice for small businesses.
Its data de-duplication feature can increase storage efficiency, and the automated data classification function ensures that critical data is appropriately secured.
2. Which is the best cloud data security software for large enterprises?
ShareArchiver is suitable for large enterprises because of its comprehensive security features, such as user activity monitoring and incident response, which can handle the complexity of a large organization’s security needs.
3. Which is the best cloud data security software for financial institutions?
Almost all cloud data security software offer features and services for financial institutions.
However, ShareArchiver is ideal for financial institutions.
Its robust data encryption and policy-based access control can protect sensitive financial data from unauthorized access and breaches.
4. Which is the best cloud data security software for public institutions?
Public institutions would benefit from ShareArchiver.
Its data de-duplication feature ensures efficient use of storage, and its comprehensive security measures maintain public trust by securing data.
5. Which is the best cloud data security software for tech startups?
ShareArchiver stands out as the best choice for tech startups.
Its user-friendly interface, policy-based access control, and automated data classification make it a convenient choice for startups.
Buyer’s Guide
What is cloud data security software?
Cloud data security software is a suite of tools and technologies designed to safeguard information stored on cloud-based platforms.
This data can include any digital information an organization stores in the cloud, such as customer data, internal files, intellectual property, etc.
These security solutions offer protection against a wide range of cyber threats, from common ones like malware and phishing to complex, advanced persistent threats (APTs).
They are designed to ensure data confidentiality, integrity, and availability, called the CIA triad, a core tenet of information security.
One way to understand the function of cloud data security software is by breaking it down into its primary responsibilities:
Confidentiality: The software helps keep sensitive data private by using encryption, tokenization, and other security measures.
Only authorized entities have access to the actual data.
Integrity: It ensures the data is accurate and reliable, protecting it from unauthorized changes.
Availability: The software assists in keeping data accessible to authorized users when needed, despite threats like DDoS attacks that could disrupt services.
Cloud data security software operates through various mechanisms to maintain the CIA triad.
These include identity and access management (IAM), which involves defining and managing individual network users’ roles and access privileges; encryption, which transforms data into a code to prevent unauthorized access; and threat detection and response systems, which identify and counteract cyber threats.
Moreover, these security solutions often can secure data-at-rest (stored data) and data-in-transit (data being transferred).
Data-at-rest is typically encrypted, while data-in-transit may be protected using SSL/TLS encryption or a secure VPN.
Another key aspect of cloud data security software is its emphasis on regulatory compliance.
Numerous industries are subject to strict data regulations, such as the Health Insurance Portability and Accountability Act (HIPAA) for healthcare or the General Data Protection Regulation (GDPR) for businesses operating in the European Union.
Cloud data security software helps organizations meet these compliance requirements by providing features like automated compliance checks and detailed reporting.
What makes great cloud data security software?
What distinguishes exceptional cloud data security software from a merely adequate one?
Organizations increasingly depend on the cloud to handle sensitive data, so choosing the right security software becomes critical.
Several factors set great cloud data security software apart from the rest.
Comprehensive Coverage: Top-tier cloud data security software provides end-to-end protection for data in various states: at rest, in use, and transit.
This comprehensive coverage entails data encryption, secure key management, tokenization, and masking capabilities.
An example would be CipherCloud’s cloud security platform, offering complete data protection across multiple cloud environments.
Real-Time Threat Intelligence: The best security software comes with real-time threat intelligence, enabling them to proactively identify and neutralize potential threats before they become significant issues.
McAfee’s MVISION Cloud, for example, uses advanced machine learning algorithms to provide real-time threat monitoring.
Identity and Access Management (IAM): IAM allows organizations to manage roles, ensure correct access privileges, and monitor user activity.
This feature is essential for preventing unauthorized data access.
Microsoft Azure, for example, offers robust IAM capabilities, allowing granular access control based on user roles.
Regulatory Compliance: Great cloud data security software will help organizations comply with industry-specific laws, regulations, and standards.
This feature often includes automatic compliance checks and detailed compliance reporting.
For example, Google Cloud’s Security Command Center helps businesses meet compliance requirements for regulations such as GDPR and HIPAA.
Scalability: As a business grows, so does the volume of its data and the complexity of managing it.
Top-tier security software must be scalable to adapt to these growing needs without sacrificing performance or security.
User-Friendliness: A solution that is difficult to understand or navigate can lead to configuration errors, reducing the effectiveness of security measures and increasing the risk of data breaches.
Great software prioritizes user-friendly interfaces and clear, intuitive controls, making it easy for administrators to manage security settings accurately.
Multi-cloud Support: Many businesses use services from multiple cloud providers, so the best cloud security software should be capable of integrating and functioning seamlessly across these varied platforms.
Automated Security: The ability to automate security tasks, such as patching vulnerabilities or responding to detected threats, is a valuable feature.
Automation improves efficiency and reduces the chances of human error leading to security vulnerabilities.
Data Loss Prevention (DLP): DLP features help ensure unauthorized users do not lose, misuse, or access sensitive data.
Good cloud security solutions should include DLP controls that are easy to set up and manage.
Vendor Reputation and Support: Finally, the software provider’s reputation and the level of customer support they provide are also important factors.
A provider with a strong reputation and a history of swift, effective customer support can be invaluable if issues arise.
How can small businesses use cloud data security software?
Cloud data security software is a critical resource for large corporations and an essential tool for small businesses.
Despite the size, every business needs to ensure the security and integrity of its data, particularly if it operates in a digital or online space.
Here’s how small businesses can effectively leverage cloud data security software:
Choosing the Appropriate Software
First and foremost, small businesses must carefully select a cloud data security software that aligns with their specific needs.
While larger corporations require a broad array of complex features, small businesses benefit more from solutions that offer essential, user-friendly security features.
This might include robust encryption, identity and access management, and threat detection and response systems.
Software like CloudCheckr or Dome9 could be good choices with their easy-to-use interfaces and comprehensive feature sets.
Securing Sensitive Data
The primary purpose of using cloud data security software is to protect sensitive information.
Small businesses deal with sensitive data, including customer information, financial records, and proprietary business data.
Cloud data security software can help protect this data through encryption and access control, ensuring that the data is accessible only to those with the right permissions.
Implementing Access Controls
Small businesses can use cloud data security software to manage who has access to different types of data.
This can be particularly useful in businesses with different roles and responsibilities.
For instance, an employee in marketing may not need access to the same data as someone in finance.
Access controls can help prevent unauthorized access and reduce the risk of insider threats.
Regulatory Compliance
Even small businesses may need to comply with various data protection regulations, depending on the nature of their work.
Cloud data security software can provide compliance monitoring and management features to help businesses meet these requirements.
For instance, if a small healthcare business must comply with HIPAA, cloud data security software could help manage patient data securely and provide audit trails.
Training and Awareness
Small businesses often lack a dedicated IT or cybersecurity team. In such cases, cloud data security software can be a crucial tool to educate employees about security best practices.
Some software may offer features like threat simulations or training modules to increase security awareness among staff.
Automated Security
Small businesses often have limited resources.
Automating security tasks, such as regular system scans or patching vulnerabilities, can save time and resources.
Most cloud data security software provides options for such automation.
Threat Monitoring and Response
Cyber threats are a constant concern, and small businesses are not immune.
Cloud data security software can provide real-time threat monitoring and automated response mechanisms, helping to protect the business even if it doesn’t have a dedicated security team.
Scalability
As a small business grows, its security needs will likely grow. Choosing cloud data security software that can scale along with the business ensures that the growing data and increased complexity can be managed effectively.
What are the pros of cloud data security software?
Cloud data security software offers a suite of tools and features designed to protect data stored in the cloud, and the benefits of such software are manifold. Here are the key advantages:
1. Enhanced Data Protection
Cloud data security software provides robust safeguards for your data, no matter where it’s stored in the cloud.
These software tools help keep your data confidential and secure through encryption, tokenization, and other security measures.
They also provide secure key management systems that maintain the secrecy and availability of encryption keys.
2. Regulatory Compliance
Compliance with data protection regulations is critical for businesses in many industries.
Non-compliance can lead to heavy fines and damage to a company’s reputation.
Cloud data security software can help businesses maintain compliance with regulations such as GDPR, HIPAA, and CCPA by providing features like automatic compliance checks and detailed compliance reports.
3. Real-time Threat Detection and Response
Advanced cloud data security software can provide real-time monitoring for potential security threats.
They use sophisticated algorithms and machine learning techniques to identify anomalies and potential threats, enabling businesses to respond promptly and mitigate damage.
4. Identity and Access Management
Cloud data security software typically include identity and access management (IAM) tools.
These tools let you control who can access your data and what they can do with it, thereby limiting the possibility of unauthorized data access.
5. Scalability and Flexibility
One of the significant advantages of cloud data security software is its scalability.
As your business grows and evolves, your security software can easily scale to meet your changing needs.
You can add more storage or advanced features without significant hardware investments or system overhauls.
6. Cost-Effective
Maintaining a full-fledged IT security team can be expensive for small to medium-sized businesses.
Cloud data security software can provide high-quality security measures at a fraction of the cost.
Plus, the software-as-a-service (SaaS) model many providers use lets you pay for only the needed features when you need them.
7. Data Recovery
A data backup can be a lifesaver in a data breach or system failure.
Many cloud data security software options include data backup and disaster recovery options, ensuring you can quickly recover and return to business during an incident.
8. Integration
Many cloud data security software tools can easily integrate with other systems and applications, enabling you to manage all your security needs from a single platform.
This integration can lead to better visibility of your security posture and more efficient security processes.
What are some cons of cloud data security software?
While cloud data security software offers significant benefits, it’s also essential to consider some potential drawbacks.
Understanding such software’s pros and cons can help businesses make informed decisions about their security strategies.
Here are some potential disadvantages of cloud data security software:
1. Dependency on the Provider
Once you’ve chosen cloud data security software, you largely depend on the provider’s capabilities and integrity.
Your data could be at risk if the provider suffers a security breach or goes out of business.
2. Costs Can Add Up
While the scalability of cloud data security software can benefit, it can also add up costs.
As your business grows or your security needs become more complex, you may need to invest more in the software, which can strain a smaller company’s budget.
3. Potential Compatibility Issues
If your business uses multiple cloud platforms or unique technologies, you might experience compatibility issues with certain cloud data security software.
Ensuring your chosen software integrates seamlessly with your existing systems is important.
4. The complexity of Settings and Configurations
Despite efforts to make these software solutions user-friendly, some businesses may still find them complex and challenging to configure correctly.
Improper configurations can lead to vulnerabilities that cybercriminals can exploit.
5. Limited Control Over Data
Using cloud-based security software may mean you need more control over your data.
Depending on the terms and conditions of the provider, you may have to comply with certain policies you don’t have control over.
6. Data Privacy Regulations
While cloud data security software helps businesses comply with data protection regulations, storing and processing data in the cloud can complicate compliance, particularly when data is stored in a different jurisdiction.
7. Need for Continuous Updates
Cyber threats and your cloud data security software must evolve rapidly.
The need for continuous updates can be a disadvantage if not handled correctly by the software provider.
In conclusion, while cloud data security software provides numerous advantages, potential drawbacks such as provider dependency, costs, compatibility issues, and limited control over data must be considered.
Businesses can select a cloud data security software that best meets their unique needs and circumstances by carefully considering these factors.
Frequently Asked Questions (FAQs)
1. How does ShareArchiver’s automated data classification help in securing data?
Automated data classification organizes data based on sensitivity, ensuring higher protection levels for sensitive data.
2. How does ShareArchiver’s policy-based access control prevent unauthorized access?
Policy-based access control allows you to define who can access certain data, reducing the risk of unauthorized access.
3. Does ShareArchiver’s user activity monitoring feature help identify potential threats?
Yes, user activity monitoring helps identify any suspicious behavior, providing an early warning for potential data breaches.
4. How does the data de-duplication feature in ShareArchiver help with data storage?
Data de-duplication removes redundant data, improving storage efficiency
5. How can ShareArchiver’s incident response feature help in a data breach?
Incident response helps quickly identify and manage a data breach, minimizing the potential damage.
6. How secure does ShareArchiver provide data encryption?
ShareArchiver uses high-level encryption to secure your data, making it almost impossible for unauthorized users to access.
7. Can ShareArchiver’s features help with compliance with data protection regulations?
Yes, features like data encryption and policy-based access control help organizations comply with various data protection regulations.
8. How user-friendly is ShareArchiver for someone with no technical background?
ShareArchiver is designed to be user-friendly, with a simple interface and comprehensive support system.
9. Can ShareArchiver scale up as my business grows?
Yes, ShareArchiver is highly scalable and can cater to the increasing security needs of your growing business